30+ data flow diagram threat model
Some of the most valuable key. Threat modeling refers to a number of systematic approaches for eliciting security and privacy threats.
![]()
Threatmodeler About The Evolution Of Threat Modeling
Swim Lane Diagrams Swim lane diagrams are a common way to represent.
. Data-flow diagram elements min. Visual Paradigm Online features an online threat model maker and a large variety of technical and. Threat modeling is an effective technique to help you identify threats and ways to reduce or eliminate risk.
This white paper looks at some flaws and the advantages of moving to a more mature Process Flow Diagram PFD approach to threat modeling as a solution. Threat modeling is a lightweight approach to reason about application security and uses Data Flow Diagrams DFDs with security annotations. It shows data sources and destinations relevant.
Data flow diagrams therefore are generated as a means of communicating this to the outside world those who are not threat modelers. Microsofts Threat Modelling Tool This tool identifies threats based on STRIDE threat model classification and is based on Data Flow Diagram DFD which can be used to. Process - The task element min.
By Laurens Sion and colleagues. UML to add trust boundaries to those diagrams than to create new diagrams just for threat modeling. In this longest episode of the worlds shortest threat modeling videos I introduce the five.
Data Flow Diagrams DFDs are the main input for threat modeling. Are Data Flow Diagrams Enough. In this step Data Flow Diagram should be divided in the context of Model View Controller MVC.
Operational or infrastructure threat models. The resulting document is the threat model for the application. Create threat models online.
A threat model diagram is a visual form of threat model. A Data Flow Diagram DFD 49 with security-speciflc annotations is used to describe how data enters leaves and traverses the system. Click on the diagram you wish to edit.
Creating the Threat Dragon diagrams Once you have created or opened an existing threat model file the next step is to edit the threat model diagrams. We extended Reexion Models to check the. User Login Data Flow Diagram for the College Library Website.
Data-flow - The data in transit. External entity - The no control element min. Data flow diagrams DFDs Threat modelling DFDs are similar to those used by system engineers with a few additional shapes.
View System as an adversary. This is the first and the foremost thing to do while modelling a system using DFD Based. Data flow diagrams are very frequently used in threat modeling.
WebRTC Data Flow Diagram Maturity Model OpenSAMM 22 requires annotating the threat model with compensating controls which include technical secu-rity measures as well. Threat Dragon TD is used to create threat model diagrams and to record possible threats. Data store - The storage element min.
This weeks threat model Thursday looks at an academic paper Security Threat Modeling. The original intent of a data flow. Approach your data-flow diagram with the right threat model focus.
Lets discuss these steps in detail one by one.

Real Time Operational Monitoring Of Renewable Energy Assets With Aws Iot Aws For Industries

Threat Modeling Demystified

Threat Modeling Demystified
What S The Difference Between A Data Flow Diagram And Use Case Diagram In Terms Of Construction And Usage Quora
How To Simplify A Complex And Frustrating Change Management Process When Delivering Software To Production Quora
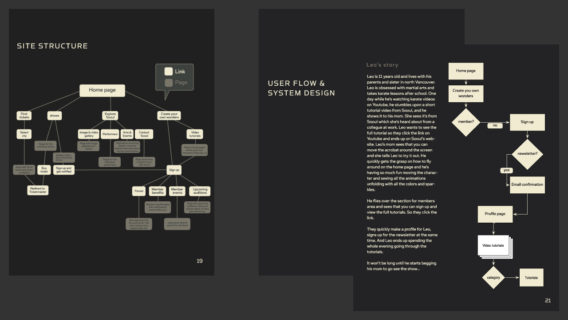
How To Design A User Flow Diagram For Your Website
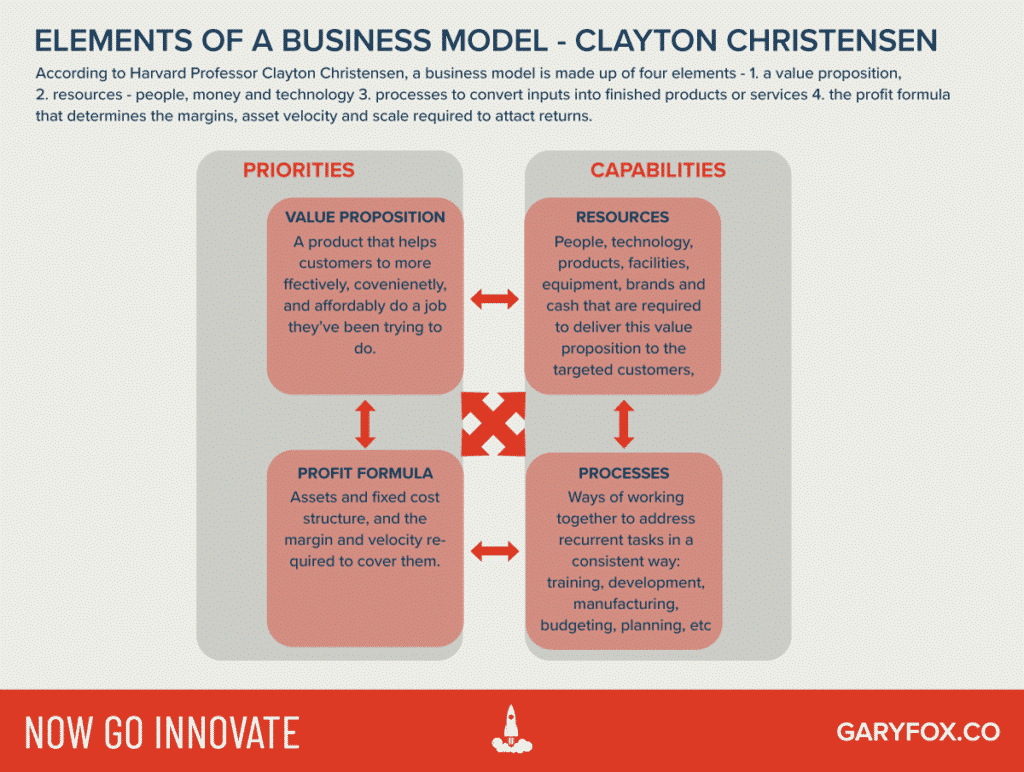
What Is A Business Model Definition Explanation 30 Examples

Threatmodeler About The Evolution Of Threat Modeling
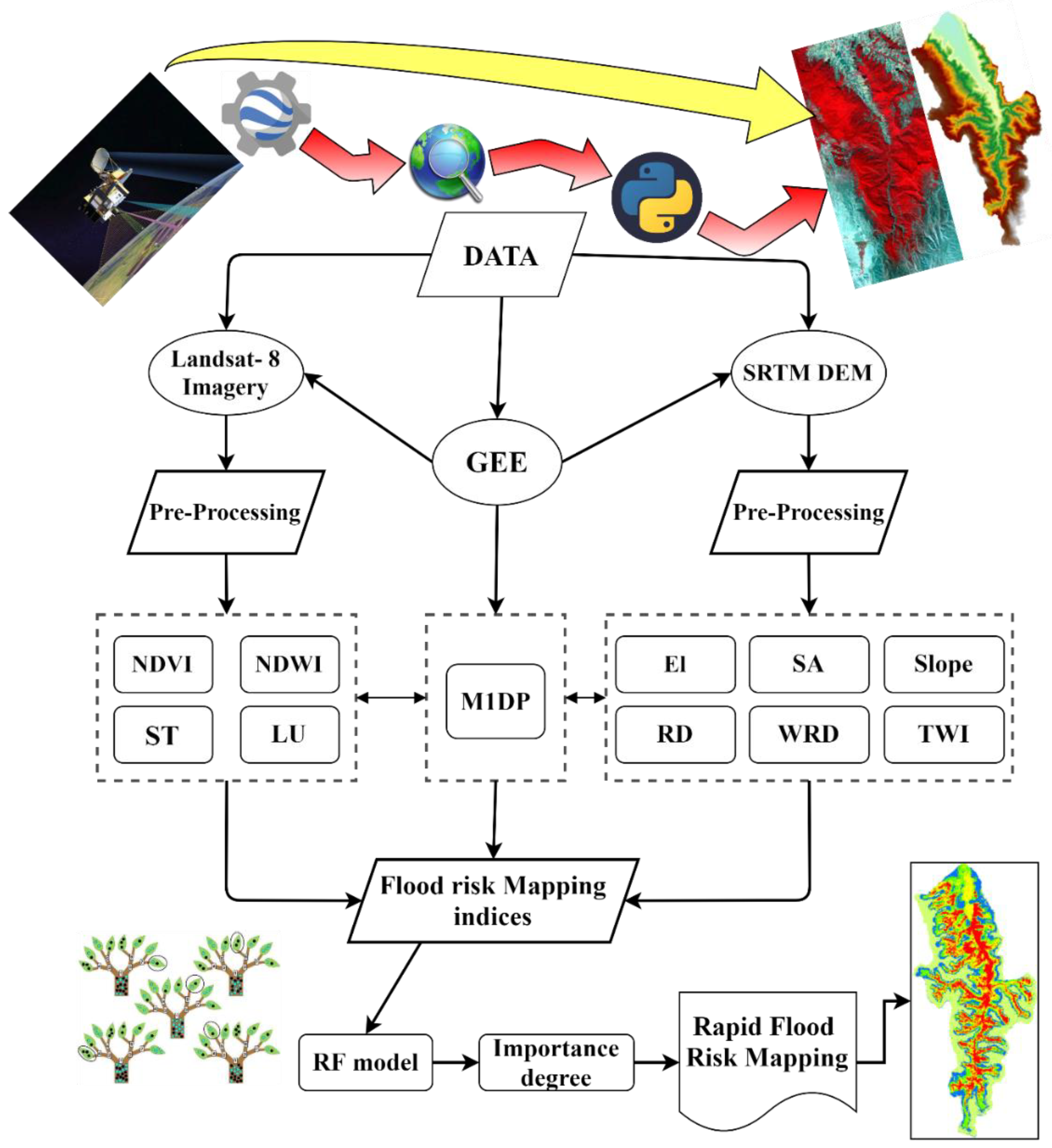
Water Free Full Text Flood Risk Mapping By Remote Sensing Data And Random Forest Technique Html

Threat Modeling Demystified

Graphing The Utility Grid On Aws Aws For Industries

Threat Modeling Demystified

Threat Modeling Demystified

A Threshold Based Real Time Analysis In Early Detection Of Endpoint Anomalies Using Siem Expertise Sciencedirect
100 Ai Use Cases Applications In Depth Guide
What Is The Purpose Of Developing Dfds Quora

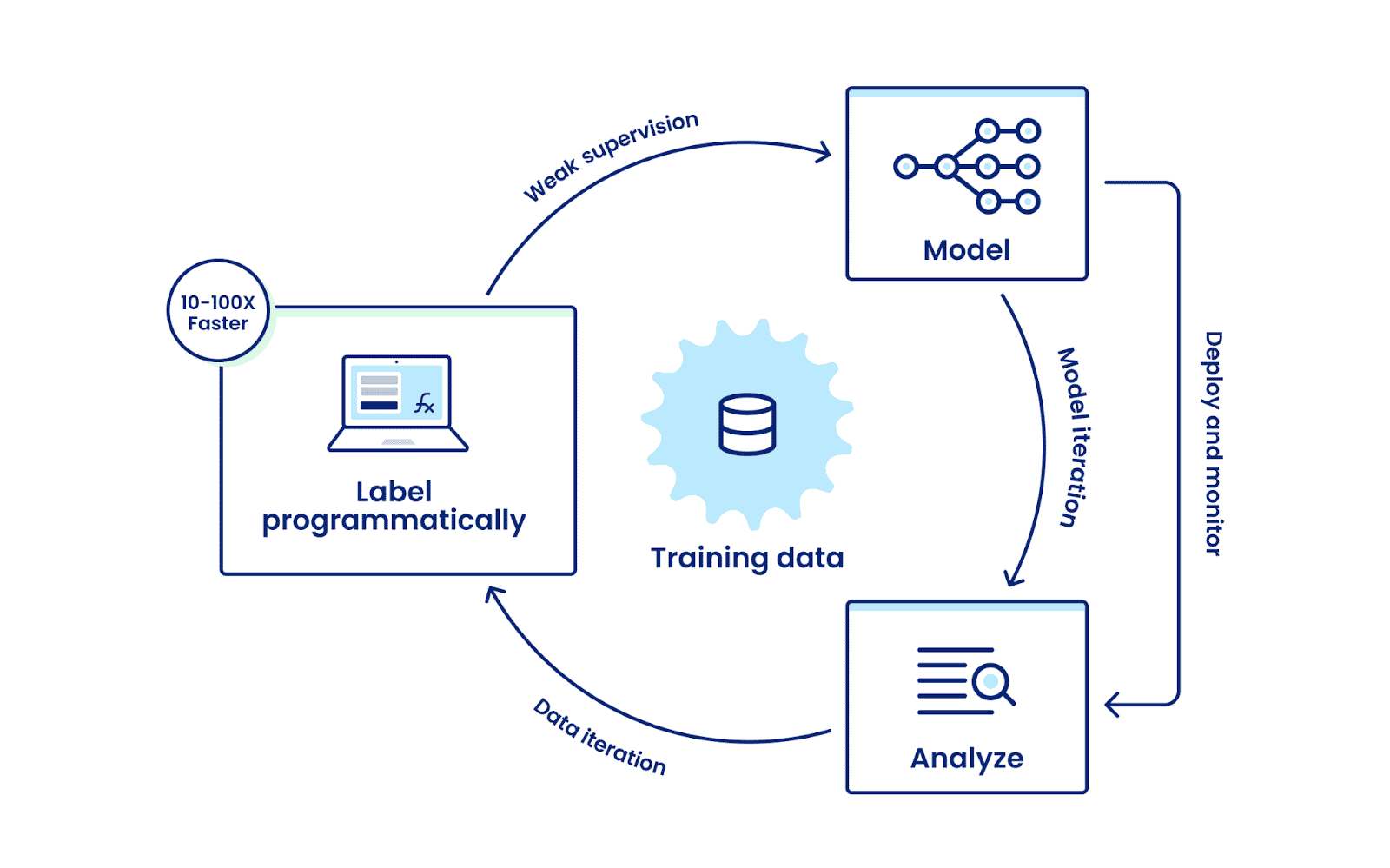
Introducing Continuous Model Feedback To Drive Rapid Data Quality Improvement Snorkel Ai